What is a DMARC Policy? A Simple Explanation
DMARC Explained: Understanding What is DMARC Policy
Domain-based Message Authentication (DMARC) is a set of email settings guidelines specifically created to make emails safer by closing loopholes long exploited by spammers and scammers. It also means, for those who send out bulk emails (brands that use email marketing), and do not follow the new DMARC guidelines, emails could be blocked completely.
In October 2023, Google and Yahoo introduced new sender requirements set to take effect on February 1, 2024. These apply to anyone who sends bulk emails to Gmail or Yahoo addresses or uses a Gmail address as their “From” address. This new authentication method is called DMARC, or “domain-based message authentication, reporting, and conformance.”
Why is DMARC Email Authentication Policy Relevant to You?
These rules matter for individuals that have an organizational email using Gmail or Yahoo servers. In other words, businesses and companies that use email marketing can be impacted.
Despite being a vital part of bulk email sends, marketers often overlook the importance of DMARC’s authentication protocols due to its technical complexity. In this blog post, we break down the DMARC email authentication protocols and requirements step-by-step to help you understand its operations, specifically:
What is DMARC?
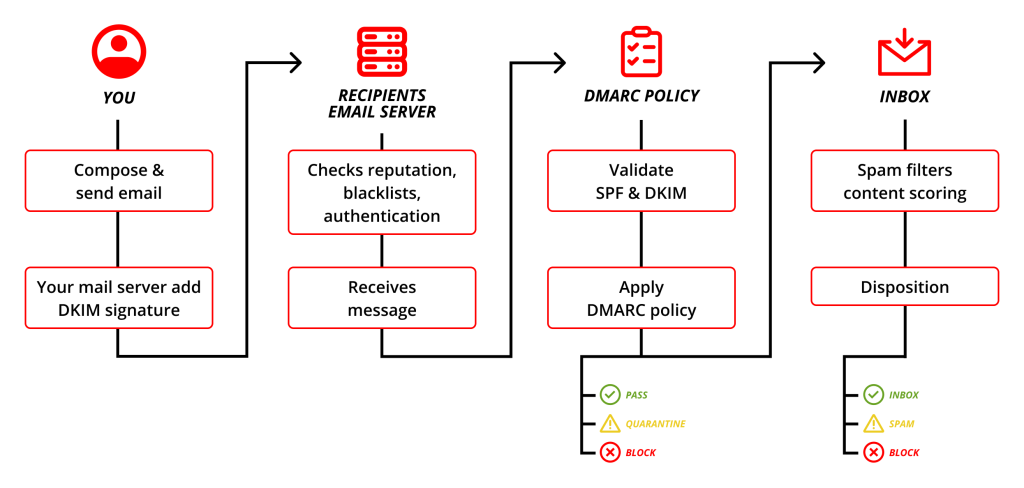
DMARC, or Domain-based Message Authentication, Reporting, and Conformance, is an email authentication standard designed to enhance the security of email communication. It is a series of tests to see if the email is coming from someone who is authorized to send it within an organization’s domain. If the mail server (for example, Google’s Gmail) finds a message from someone who does not have permission to send an email on your company’s behalf, the DMARC test “fails” this message and the email never reaches the receiver’s inbox.
How Does DMARC Work?
DMARC email authentication works alongside other email authentication methods including SPF (Sender Policy Framework) and DKIM (DomainKeys Identified Mail) to validate the authenticity of receivers’ emails. As such, you can think of DMARC email authentication as a third layer of security for both your company and its end-users.
- DKIM: adds a digital signature to every outgoing email message which allows receiving servers to verify that the message actually came from your organization.
- Role with DMARC: DMARC ensures the header “From:” domain matches the d=domain in the DKIM signature. Validates authenticity of the message
- SPF: specifies authorized servers and domains which can send emails on behalf of your organization.
- Role with DMARC: DMARC ensures the header “From:” address matches the return path or envelope “From:” address in the SPF record. Validates the source of the email
DMARC has three settings for failed validation: quarantine, reject, and none. The DMARC email authentication security process determines which three of these phases will be applied to the message. The email server administrator sets up DMARC settings, so what happens to failed messages depends on administrator preferences.
- Quarantine: When an email message fails validation and is placed in the spam folder
- Reject: Email fails DMARC authentication and is deleted
- None: Nothing happens, and the email message is sent to the end-user’s inbox
In addition to authentication policies, DMARC uses robust reporting mechanisms. These reports send feedback and insights about the status of email in your domain. Here, you can see who is sending unauthorized emails and take down malicious-intended sources.
This feedback loop allows organizations to monitor and improve their email security, creating an effective defense against phishing attacks and unauthorized use of their domains in fraudulent email campaigns. DMARC has become a critical tool for businesses and organizations seeking to fortify their email communication channels and protect both their brand reputation and the privacy of their users.
Verifying your emails, enabling effortless unsubscribing, and ensuring compliance with spam thresholds may seem daunting. However, rest assured, these updates will require only a few minutes of your time or that of your IT team, and we will guide you through the general requirements.
DMARC Email Authentication Requirements
- Requirement #1: You’ll need to have the right authentication for the email domain you’re sending from. To ensure legitimacy of your emails, make sure Sender Policy Framework (SPF), Domain-based Message Authentication, Reporting & Conformance (DMARC), and DomainKeys Identified Mail (DKIM) are correctly set up. SPF is already set up on all of our sender IP domain names, so you’re good to go there. DMARC uses DKIM to verify the authenticity of your emails.
- If you have a custom domain, you’ll need to set up DMARC and DKIM to help ensure your emails reach your recipients’ inboxes.
- No custom domain? No further action is needed for this requirement.
- Requirement #2: You must include a one-click unsubscribe link in your email. All bulk emails must include an easy one-click unsubscribe option and honor requests within two days.
- Requirement #3: Your spam rates will need to fall below a certain threshold. Google and Yahoo will begin enforcing a spam rate threshold that senders must stay under to ensure Gmail and Yahoo recipients aren’t being sent spam.
For more specific steps to adding your DMARC record, click here.
Ready Artwork Will Help You Set Up Email Campaigns that Follow DMARC Protocols
Ready Artwork has 20+ years of digital marketing and email marketing success. We can help you send targeted emails, analyze results, grow your business, engage customers while following the DMARC guidelines and protocols. Start a conversation by filling out this form:
Contact Us
DROP US A MESSAGE
WE'LL GET BACK TO YOU SOON!



